Legal Representation
Attorney
Alicia A. Matusheski
USPTO Deadlines
Next Deadline
2135 days remaining
Section 8 Declaration Due (Principal Register) (Based on registration date 20251021)
Due Date
October 21, 2031
Grace Period Ends
April 21, 2032
Additional deadlines exist. Contact your attorney for complete deadline information.
Application History
11 events| Date | Code | Type | Description | Documents |
|---|---|---|---|---|
| Oct 21, 2025 | NRCC | E | NOTICE OF REGISTRATION CONFIRMATION EMAILED | Loading... |
| Oct 21, 2025 | R.PR | A | REGISTERED-PRINCIPAL REGISTER | Loading... |
| Sep 2, 2025 | NPUB | E | OFFICIAL GAZETTE PUBLICATION CONFIRMATION E-MAILED | Loading... |
| Sep 2, 2025 | PUBO | A | PUBLISHED FOR OPPOSITION | Loading... |
| Aug 27, 2025 | NONP | E | NOTIFICATION OF NOTICE OF PUBLICATION E-MAILED | Loading... |
| Jul 30, 2025 | CNSA | O | APPROVED FOR PUB - PRINCIPAL REGISTER | Loading... |
| Jul 28, 2025 | DOCK | D | ASSIGNED TO EXAMINER | Loading... |
| Jul 18, 2025 | MDSM | E | NOTICE OF DESIGN SEARCH CODE E-MAILED | Loading... |
| Jul 18, 2025 | NWOS | I | NEW APPLICATION OFFICE SUPPLIED DATA ENTERED | Loading... |
| Feb 24, 2025 | NWAP | I | NEW APPLICATION ENTERED | Loading... |
| Feb 24, 2025 | MAFR | O | APPLICATION FILING RECEIPT MAILED | Loading... |
Detailed Classifications
Class 042
Application service provider (ASP) featuring software using artificial intelligence for cybersecurity breach or insider threat detection and automated response; Computer programming consultancy in the field of cybersecurity breach or insider threat detection and automated response; Computer software development, computer programming and maintenance of computer software for cybersecurity breach or insider threat detection and automated response, and access management; Consultancy in the field of artificial intelligence technology; Consulting in the field of information technology; Consulting in the field of virtualization technologies for enterprises and businesses; Cybersecurity services in the nature of restricting unauthorized access to computer systems, data, and apps; Development of customized software for others for use in risk assessment, information security, business analysis, audit and audit planning, and sales management; Platform as a service (PAAS) featuring computer software platforms for cybersecurity breach or insider threat detection and automated response, and access management; Providing a website featuring non-downloadable software using artificial intelligence for cybersecurity breach or insider threat detection and automated response; Providing temporary use of a web-based software application for cybersecurity breach or insider threat detection and automated response, and access management; Providing temporary use of non-downloadable cloud-based software for cybersecurity; Providing temporary use of nondownloadable web-based decentralized applications (DApps) for cybersecurity breach or insider threat detection and automated response, and access management; Providing temporary use of on-line nondownloadable cloud computing software using artificial intelligence for cybersecurity breach or insider threat detection and automated response, and access management; Providing temporary use of on-line non-downloadable cloud computing software for cybersecurity; Providing temporary use of on-line nondownloadable opensource software for cybersecurity breach or insider threat detection and automated response, and access management; Providing temporary use of on-line non-downloadable software and applications using artificial intelligence for cybersecurity breach or insider threat detection and automated response, and access management; Technology consultation in the field of artificial intelligence; Technology consultation in the field of cybersecurity; Computer technology consultancy in the field of cybersecurity; Technical consulting services in the fields of datacenter architecture, public and private cloud computing solutions, and evaluation and implementation of internet technology and services
First Use Anywhere:
May 25, 2023
First Use in Commerce:
May 31, 2023
Additional Information
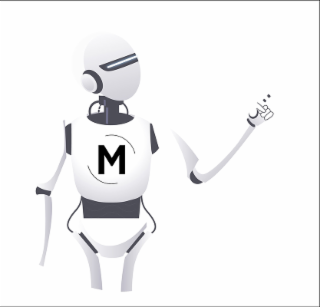
Design Mark
The mark consists of a robot character with a logo on its chest consisting of the letter "M" enclosed within two curved lines. The robot is depicted standing and looking to the left, and has one arm raised with its index finger pointed.
Pseudo Mark
MIMOTO
Classification
International Classes
042