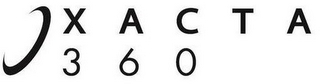Legal Representation
Attorney
David R. Schaffer
USPTO Deadlines
Next Deadline
905 days remaining
Section 8 & 9 Renewal Due (Principal Register) (Based on registration date 20180710)
Due Date
July 10, 2028
Grace Period Ends
January 10, 2029
Application History
23 events| Date | Code | Type | Description | Documents |
|---|---|---|---|---|
| Dec 11, 2024 | NA85 | E | NOTICE OF ACCEPTANCE OF SEC. 8 & 15 - E-MAILED | Loading... |
| Dec 11, 2024 | C15A | O | REGISTERED - SEC. 8 (6-YR) ACCEPTED & SEC. 15 ACK. | Loading... |
| Dec 11, 2024 | APRE | A | CASE ASSIGNED TO POST REGISTRATION PARALEGAL | Loading... |
| Jul 5, 2024 | E815 | I | TEAS SECTION 8 & 15 RECEIVED | Loading... |
| Jul 10, 2023 | REM1 | E | COURTESY REMINDER - SEC. 8 (6-YR) E-MAILED | Loading... |
| Dec 9, 2020 | ASCK | I | ASSIGNMENT OF OWNERSHIP NOT UPDATED AUTOMATICALLY | Loading... |
| Jul 10, 2018 | R.PR | A | REGISTERED-PRINCIPAL REGISTER | Loading... |
| Jun 6, 2018 | SUNA | E | NOTICE OF ACCEPTANCE OF STATEMENT OF USE E-MAILED | Loading... |
| Jun 5, 2018 | CNPR | P | ALLOWED PRINCIPAL REGISTER - SOU ACCEPTED | Loading... |
| Jun 5, 2018 | SUPC | I | STATEMENT OF USE PROCESSING COMPLETE | Loading... |
| May 14, 2018 | IUAF | S | USE AMENDMENT FILED | Loading... |
| Jun 5, 2018 | AITU | A | CASE ASSIGNED TO INTENT TO USE PARALEGAL | Loading... |
| May 14, 2018 | EISU | I | TEAS STATEMENT OF USE RECEIVED | Loading... |
| May 9, 2018 | ASCK | I | ASSIGNMENT OF OWNERSHIP NOT UPDATED AUTOMATICALLY | Loading... |
| Nov 21, 2017 | NOAM | E | NOA E-MAILED - SOU REQUIRED FROM APPLICANT | Loading... |
| Sep 26, 2017 | NPUB | E | OFFICIAL GAZETTE PUBLICATION CONFIRMATION E-MAILED | Loading... |
| Sep 26, 2017 | PUBO | A | PUBLISHED FOR OPPOSITION | Loading... |
| Sep 6, 2017 | NONP | E | NOTIFICATION OF NOTICE OF PUBLICATION E-MAILED | Loading... |
| Aug 17, 2017 | CNSA | P | APPROVED FOR PUB - PRINCIPAL REGISTER | Loading... |
| Aug 17, 2017 | DOCK | D | ASSIGNED TO EXAMINER | Loading... |
| Jun 27, 2017 | MDSM | E | NOTICE OF DESIGN SEARCH CODE E-MAILED | Loading... |
| Jun 26, 2017 | NWOS | I | NEW APPLICATION OFFICE SUPPLIED DATA ENTERED | Loading... |
| Jun 22, 2017 | NWAP | I | NEW APPLICATION ENTERED | Loading... |
Detailed Classifications
Class 009
Computer software and downloadable computer software for Information Technology (IT) asset management, namely, cataloging and managing of IT physical and logical business assets; computer software and downloadable computer software for IT risk management, namely, assessing and managing IT risks in context of the business, and presenting risk exposure thereto; computer software and downloadable computer software for IT vulnerability management, namely, detecting and remediating vulnerabilities and related threats across physical and logical IT assets, through the integration into a security tools architecture; computer software and downloadable computer software for IT control management, namely, documenting, assessing, and providing an evidence trail of IT controls and compliance with standards and regulations; all in the fields of information assurance, information security, cybersecurity, operational security, computer network data analytics, secure wireless networking and secure mobility, identity management, secure message handling, secure LAN data integration, and organizational enterprise risk management relating to network security, communication security and data security
First Use Anywhere:
Aug 21, 2017
First Use in Commerce:
Aug 21, 2017
Class 042
Providing temporary use of non-downloadable software for Information Technology (IT) asset management, namely, cataloging and managing of IT physical and logical business assets; providing temporary use of non-downloadable software for IT risk management, namely, assessing and managing IT risks in context of the business, and presenting risk exposure thereto; providing temporary use of non-downloadable software for IT vulnerability management, namely, detecting and remediating vulnerabilities and related threats across physical and logical IT assets, through the integration into a security tools architecture; providing temporary use of non-downloadable software for IT control management, namely, documenting, assessing, and providing an evidence trail of IT controls and compliance with standards and regulations; all in the fields of information assurance, information security, cybersecurity, operational security, computer network data analytics, secure wireless networking and secure mobility, identity management, secure message handling, secure LAN data integration, and organizational enterprise risk management relating to network security, communication security and data security; Software as a service (SAAS) services featuring software for Information Technology (IT) asset management, namely, cataloging and managing of IT physical and logical business assets; Software as a service (SAAS) services featuring software for IT risk management, namely, assessing and managing IT risks in context of the business, and presenting risk exposure thereto; Software as a service (SAAS) services featuring software for IT vulnerability management, namely, detecting and remediating vulnerabilities and related threats across physical and logical IT assets, through the integration into a security tools architecture; Software as a service (SAAS) services featuring software for IT control management, namely, documenting, assessing, and providing an evidence trail of IT controls and compliance with standards and regulations; all in the fields of information assurance, information security, cybersecurity, operational security, computer network data analytics, secure wireless networking and secure mobility, identity management, secure message handling, secure LAN data integration, and organizational enterprise risk management relating to network security, communication security and data security
First Use Anywhere:
Jul 28, 2017
First Use in Commerce:
Jul 28, 2017
Additional Information
Design Mark
The mark consists of a canted crescent design with the open portion facing to the left and the word "XACTA" stacked above the number "360" to the right of the canted crescent design.
Color Claim
Color is not claimed as a feature of the mark.
Pseudo Mark
XACTA THREE SIXTY
Classification
International Classes
009
042